Ok, now i'll try to do Information Gathering again.
I'll try to get information from 3 domain.
That is..
1. is2c-dojo.com
2. is2c-dojo.net
3. spentera.com
First, i try to find information about is2c-dojo.com with who.is.
With who.is, we can get many information like :
- IP address
- Creation Date
- Expiration Date
- Registrar
- Name Servers
- Server Type
- Website Status
- Domain servers
- Registrant Data
- Contact Persons
- etc.
After i search it, i found the information like this.
After i get an IP address from that domain, i try to find the port which opened in that domain.
I try with zenmap with IP address 67.222.154.106.
and the result is like this.
From the information above, i found there are 9 ports and services opened in that IP address.
There are :
- port 21 service ftp
- port 53 service domain
- port 80 service http
- port 110 service pop3
- port 143 service imap
- port 443 service http
- port 993 service imap
- port 995 service pop3
- port 25 service smtp
Next, i try to to find information about is2c-dojo.net
And i got some information like this.
After i get an IP address from that domain, i try to find the port which opened in that domain.
I try with zenmap with IP address 74.81.66.104
and the result is like this
Starting Nmap 5.61TEST4 ( http://nmap.org ) at 2012-01-25 23:37 WIT
NSE: Loaded 87 scripts for scanning.
NSE: Script Pre-scanning.
Initiating Ping Scan at 23:37
Scanning 74.81.66.104 [4 ports]
Completed Ping Scan at 23:37, 0.46s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 23:37
Completed Parallel DNS resolution of 1 host. at 23:37, 0.36s elapsed
Initiating SYN Stealth Scan at 23:37
Scanning server28.web-hosting.com (74.81.66.104) [1000 ports]
Discovered open port 443/tcp on 74.81.66.104
Discovered open port 21/tcp on 74.81.66.104
Discovered open port 143/tcp on 74.81.66.104
Discovered open port 80/tcp on 74.81.66.104
Discovered open port 53/tcp on 74.81.66.104
Discovered open port 995/tcp on 74.81.66.104
Discovered open port 993/tcp on 74.81.66.104
Discovered open port 110/tcp on 74.81.66.104
SYN Stealth Scan Timing: About 23.60% done; ETC: 23:39 (0:01:40 remaining)
SYN Stealth Scan Timing: About 24.73% done; ETC: 23:41 (0:03:06 remaining)
SYN Stealth Scan Timing: About 25.77% done; ETC: 23:43 (0:04:22 remaining)
Increasing send delay for 74.81.66.104 from 0 to 5 due to 11 out of 26 dropped probes since last increase.
SYN Stealth Scan Timing: About 26.93% done; ETC: 23:45 (0:05:28 remaining)
SYN Stealth Scan Timing: About 28.03% done; ETC: 23:46 (0:06:28 remaining)
SYN Stealth Scan Timing: About 29.13% done; ETC: 23:47 (0:07:20 remaining)
Increasing send delay for 74.81.66.104 from 5 to 10 due to 11 out of 11 dropped probes since last increase.
SYN Stealth Scan Timing: About 30.27% done; ETC: 23:49 (0:08:06 remaining)
SYN Stealth Scan Timing: About 31.37% done; ETC: 23:50 (0:08:47 remaining)
SYN Stealth Scan Timing: About 32.57% done; ETC: 23:51 (0:09:27 remaining)
SYN Stealth Scan Timing: About 34.13% done; ETC: 23:53 (0:10:10 remaining)
SYN Stealth Scan Timing: About 36.23% done; ETC: 23:54 (0:10:56 remaining)
SYN Stealth Scan Timing: About 39.53% done; ETC: 23:57 (0:11:48 remaining)
SYN Stealth Scan Timing: About 62.63% done; ETC: 00:06 (0:10:48 remaining)
SYN Stealth Scan Timing: About 69.40% done; ETC: 00:08 (0:09:20 remaining)
SYN Stealth Scan Timing: About 75.37% done; ETC: 00:09 (0:07:48 remaining)
SYN Stealth Scan Timing: About 81.03% done; ETC: 00:10 (0:06:11 remaining)
SYN Stealth Scan Timing: About 86.43% done; ETC: 00:10 (0:04:32 remaining)
SYN Stealth Scan Timing: About 91.67% done; ETC: 00:11 (0:02:50 remaining)
SYN Stealth Scan Timing: About 96.77% done; ETC: 00:12 (0:01:07 remaining)
Completed SYN Stealth Scan at 00:12, 2100.21s elapsed (1000 total ports)
Initiating Service scan at 00:12
Scanning 8 services on server28.web-hosting.com (74.81.66.104)
Completed Service scan at 00:12, 5.00s elapsed (8 services on 1 host)
Initiating OS detection (try #1) against server28.web-hosting.com (74.81.66.104)
Retrying OS detection (try #2) against server28.web-hosting.com (74.81.66.104)
NSE: Script scanning 74.81.66.104.
Initiating NSE at 00:12
Completed NSE at 00:15, 144.34s elapsed
Nmap scan report for server28.web-hosting.com (74.81.66.104)
Host is up (0.50s latency).
Not shown: 990 filtered ports
PORT STATE SERVICE VERSION
20/tcp closed ftp-data
21/tcp open ftp?
|_ftp-bounce: no banner
53/tcp open domain?
80/tcp open http?
110/tcp open pop3?
143/tcp open imap?
| imap-capabilities:
|_ ERROR: Failed to connect to server
443/tcp open https?
|_ssl-cert: TIMEOUT
587/tcp closed submission
993/tcp open imaps?
|_ssl-cert: TIMEOUT
995/tcp open pop3s?
|_ssl-cert: TIMEOUT
OS fingerprint not ideal because: Didn't receive UDP response. Please try again with -sSU
No OS matches for host
TRACEROUTE
HOP RTT ADDRESS
1 503.78 ms server28.web-hosting.com (74.81.66.104)
NSE: Script Post-scanning.
Read data files from: /usr/local/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 2267.86 seconds
Raw packets sent: 3371 (154.316KB) | Rcvd: 17 (720B)
From the information above, i found there are 8 ports and services opened in that IP address.
There are :
- Port 21 service ftp
- Port 53 service domain
- Port 80 service http
- Port 110 service pop3
- Port 143 service imap
- Port 443 service https
- Port 993 service imaps
- Port 995 service pop3s
After i get an IP address from that domain, i try to find the port which opened in that domain.
I try with zenmap with IP address 72.14.204.121.
and the result is like this.
Starting Nmap 5.61TEST4 ( http://nmap.org ) at 2012-01-25 23:36 WIT
NSE: Loaded 87 scripts for scanning.
NSE: Script Pre-scanning.
Initiating Ping Scan at 23:36
Scanning 72.14.204.121 [4 ports]
Completed Ping Scan at 23:36, 0.37s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 23:36
Completed Parallel DNS resolution of 1 host. at 23:36, 0.21s elapsed
Initiating SYN Stealth Scan at 23:36
Scanning iad04s01-in-f121.1e100.net (72.14.204.121) [1000 ports]
Discovered open port 80/tcp on 72.14.204.121
Completed SYN Stealth Scan at 23:36, 24.31s elapsed (1000 total ports)
Initiating Service scan at 23:36
Scanning 1 service on iad04s01-in-f121.1e100.net (72.14.204.121)
Completed Service scan at 23:36, 7.72s elapsed (1 service on 1 host)
Initiating OS detection (try #1) against iad04s01-in-f121.1e100.net (72.14.204.121)
Retrying OS detection (try #2) against iad04s01-in-f121.1e100.net (72.14.204.121)
NSE: Script scanning 72.14.204.121.
Initiating NSE at 23:36
Completed NSE at 23:37, 20.07s elapsed
Nmap scan report for iad04s01-in-f121.1e100.net (72.14.204.121)
Host is up (0.31s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Google httpd 2.0 (GFE)
|_http-title: Error 404 (Not Found)!!1
|_http-methods: No Allow or Public header in OPTIONS response (status code 404)
113/tcp closed ident
OS fingerprint not ideal because: Didn't receive UDP response. Please try again with -sSU
No OS matches for host
Uptime guess: 0.000 days (since Wed Jan 25 23:36:40 2012)
TCP Sequence Prediction: Difficulty=260 (Good luck!)
IP ID Sequence Generation: Randomized
Service Info: OS: Linux; CPE: cpe:/o:linux:kernel
TRACEROUTE
HOP RTT ADDRESS
1 309.43 ms iad04s01-in-f121.1e100.net (72.14.204.121)
NSE: Script Post-scanning.
Read data files from: /usr/local/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 65.53 seconds
Raw packets sent: 2071 (95.048KB) | Rcvd: 47 (2.396KB)
From the information above, i found there are 1 port and service opened in that IP address.
There are port 80 and the services is http.
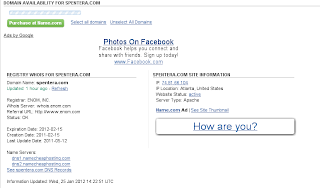
Next, i try to to find information about spentera.com
And i got some information like this.









No comments:
Post a Comment