Today, i've learning about Vulnerability Assesment and Exploitation in my class.
Vulnerability is a weakness that allows attacker to enter and get access into the targeted computer.
an Example for Software Vulnerability is Buffer Overflow. And then the example of Human Vulnerability is Secure Awareness of that person and then an example of Hardware Vulnerability is Unsecured or Unprotected from that hardware.
In this session i've use tools Nessus and exploitdb in Backtrack 5 R1.
Ok, first, i'll try to do Information gathering step to search an interesting host which have the most service.
In this step, i use zenmap tools.
After scanning that, i got 1 interesting host. That was host with IP address 192.168.0.67
Ok, next step is scan Vulnerability Assesment with Nessus. After finishing scan, i got a report like this.
From that report, i choose the port which have high risk vulnerability.
After i look the report, i use port 22 with protocol tcp and the service was openSSH.
next, i use exploitDB tools.
exploitDB tools located in Apps -> Exploitation Tools -> Open Source Exploitation -> ExploitDB -> exploitdb search.
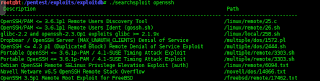
Then typed ./searchploit openssh and i get the result like this
Next we try to see a file 26.sh which located in /linux/remote/26.sh
Then typed command cd platform/linux/remote
After that typed cat 26.sh and there will be seen what the content in that file like the picture below.







No comments:
Post a Comment